创建证书
由于自动生成的证书 chrome 不允许访问,所以使用自己生成的证书。
1
2
3
4
5
| [root@master-1 ~]# mkdir certs
[root@master-1 ~]# (umask 077
[root@master-1 ~]# openssl req -nodes -newkey rsa:2048 -keyout certs/tls.key -out certs/tls.csr -subj "/C=/ST=/L=/O=/OU=/CN=kubernetes-dashboard"
[root@master-1 ~]# openssl x509 -req -sha256 -days 365 -in certs/tls.csr -signkey certs/tls.key -out certs/tls.crt
[root@master-1 ~]# kubectl create secret generic kubernetes-dashboard-certs --from-file=$HOME/certs -n kubernetes-dashboard
|
创建 Kubernetes dashboard
1
2
3
4
5
6
7
8
9
| [root@master-1 ~]# curl -sSLO https:
新增如下参数:
containers:
- args:
- --tls-cert-file=/tls.crt
- --tls-key-file=/tls.key
--auto-generate-certificates 可以保留在原处作备用。
|
1
2
3
4
| [root@master-1 ~]
[root@master-1 ~]
更改 `type: ClusterIP` 为 `type: NodePort` 并保存
|
创建 admin 账户
1
2
3
4
5
6
7
8
| cat <<EOF | kubectl apply -f -
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin-user
namespace: kubernetes-dashboard
EOF
|
绑定集群角色
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| cat <<EOF | kubectl apply -f -
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: admin-user
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: admin-user
namespace: kubernetes-dashboard
EOF
|
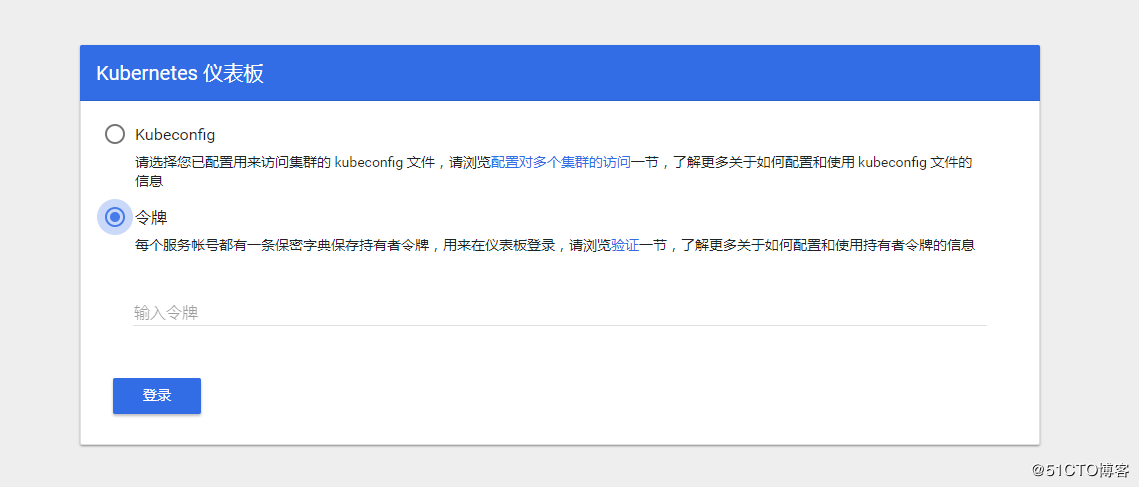
获取 token ,通过 https 进行 dashboard 端口访问
1
| kubectl -n kubernetes-dashboard get secret $(kubectl -n kubernetes-dashboard get sa/admin-user -o jsonpath="{.secrets[0].name}") -o go-template="{{.data.token | base64decode}}"
|